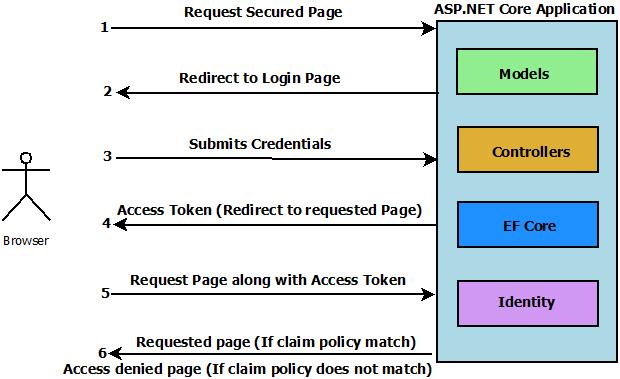
Broken Access Control in ASP.NET Core – OWASP Top 10
In this article we will learn about what is the broken access control in ASP.NET Core, why is it important, and which vulnerabilities are covered under broken access control in ASP.NET Core. We will also learn about how attackers can…